Securing your VPS with Fail2ban – How to install and configure Fail2ban on Ubuntu 20.04 VPS

Securing your VPS is essential to protect your system from malicious attacks. Among the most common threats is brute-force attacks, where hackers repeatedly attempt to guess passwords to gain unauthorized access. Fail2ban is an excellent open-source tool that safeguards your VPS against such attacks. It automatically monitors log files and blocks suspicious IP addresses. This article provides a detailed guide on how to install and configure Fail2ban on Ubuntu 20.04 VPS to enhance its security.
What is Fail2ban?
Fail2ban is an open-source security software designed to protect servers from brute-force attacks and other unauthorized login attempts. It works by monitoring system log files and automatically banning IP addresses that exhibit suspicious behavior. When an IP exceeds the configured threshold of failed login attempts, Fail2ban adds it to the firewall’s blocklist to prevent further connections.
Why Use Fail2ban?
- Protection Against Brute-Force Attacks
Fail2ban prevents brute-force attacks on services like SSH, FTP, or any other service that generates login logs. - Automatic Blocking of Suspicious IPs
Fail2ban automatically blocks IP addresses exhibiting suspicious behavior, sparing administrators from manual intervention. - Customizable Configuration
You can configure Fail2ban to protect specific services and adjust parameters such as maximum retry attempts, ban duration, and detection window. - Reduced System Load
By automating the handling of brute-force attacks, Fail2ban reduces the administrative burden, allowing system administrators to focus on other tasks.
How to install and configure Fail2ban on Ubuntu 20.04 VPS
Step 1: Log in and Update Your VPS
If you don’t already have a VPS, you can purchase one at DaintyCloud.com.
Before installing any software, ensure your system is up to date:
sudo apt update && sudo apt upgrade –y
Step 2: Install Fail2ban
Fail2ban is included in the default Ubuntu 20.04 repositories. Install it using the following command:
sudo apt install fail2ban –y
To check the installed version of Fail2ban:
fail2ban-client –v
Step 3: Verify the Fail2ban Service
After installation, Fail2ban starts automatically. Check its status with:
sudo systemctl status fail2ban
You should see an “active (running)” status if the service is running correctly.
Step 4: Configure Fail2ban
Fail2ban’s default configuration may not suit your requirements. Adjust its settings to protect your desired services.
Tip: Instead of editing the default jail.conf file directly, copy it to jail.local to preserve your changes during updates:
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Open the jail.local file for editing:
sudo nano /etc/fail2ban/jail.local
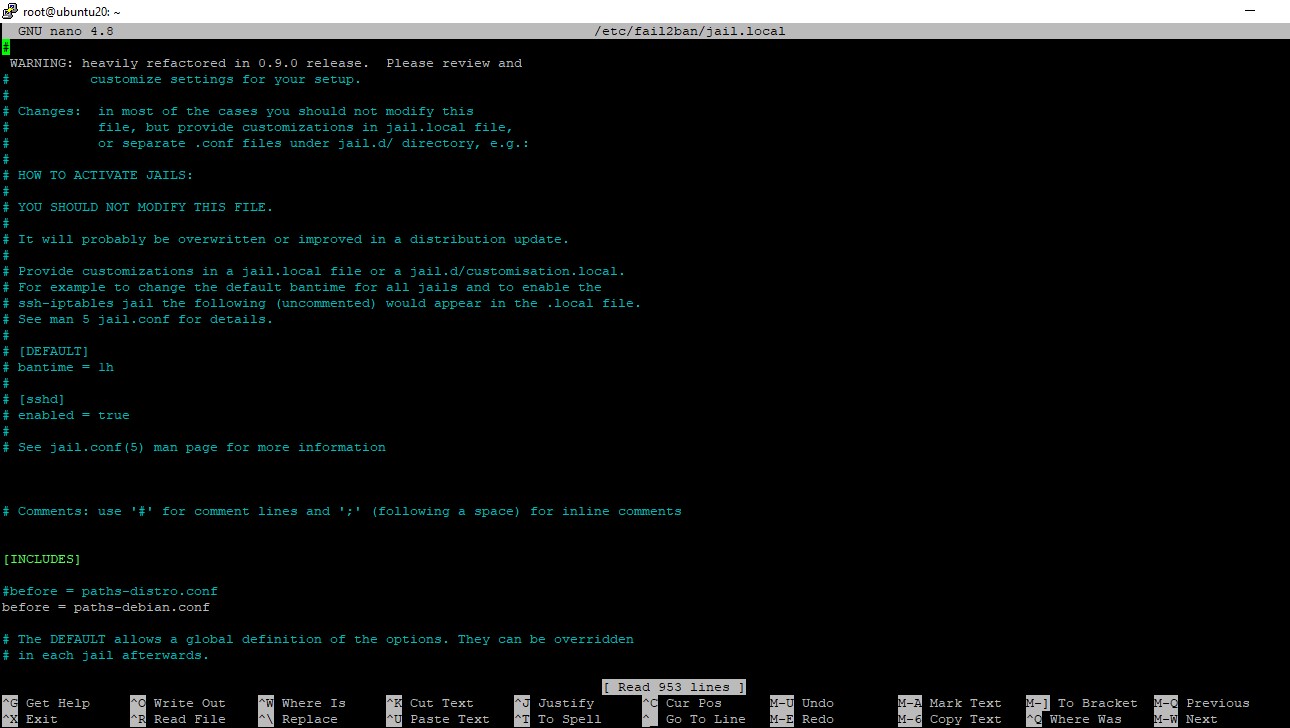
Configure the following parameters:
enabled: Enable or disable protection for a service (true to enable, false to disable).port: Specify the service’s listening port (e.g., ssh, port 22).logpath: Define the path to the log file Fail2ban will monitor.maxretry: Set the maximum number of failed attempts before banning.bantime: Specify the ban duration in seconds.findtime: Define the time window (in seconds) to monitor for failed attempts.
Save the changes by pressing Ctrl + X => then Y => Enter.
Step 5: Restart Fail2ban
After making changes, restart the Fail2ban service to apply them:
sudo systemctl restart fail2ban
Step 6: Check Fail2ban Status
To view Fail2ban’s active status and protected “jails” (services), use:
sudo fail2ban-client status
To check the status of a specific service (e.g., SSH):
sudo fail2ban-client status sshd
Step 7: Monitor Fail2ban Logs
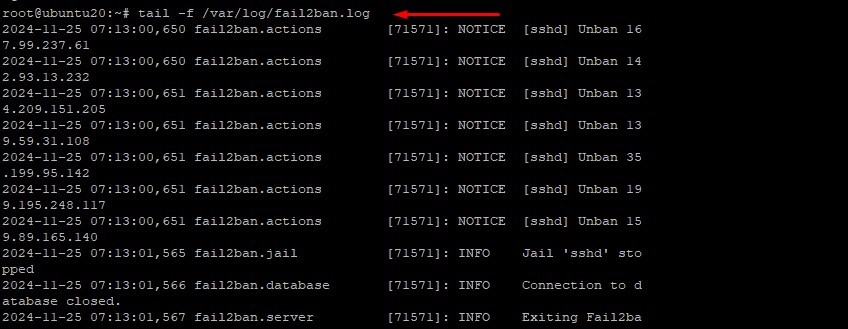
To review Fail2ban logs for details about blocked IPs and actions taken:
sudo tail -f /var/log/fail2ban.log
Step 8: Configure Firewall (Optional)
Fail2ban integrates with iptables or firewalld to block IPs. If you use UFW (Uncomplicated Firewall) on Ubuntu, ensure it allows Fail2ban to block IPs effectively:
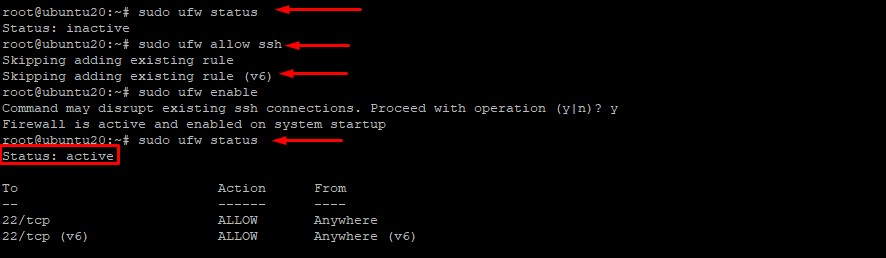
- Check UFW status:
sudo ufw status
- Allow SSH if not already enabled:
sudo ufw allow ssh
sudo ufw enable
Conclusion
Fail2ban is a powerful security tool that protects your VPS from brute-force attacks and other security threats. By configuring Fail2ban on your Ubuntu 20.04 VPS, you can automatically block unauthorized login attempts and minimize manual intervention. Follow the steps outlined in this guide to enhance the security of your VPS and safeguard it against potential threats.

